HP Inc. Friday released The Evolution of Cybercrime: Why the Dark Web is Supercharging the Threat Landscape and How to Fight Back – an HP Wolf Security Report.
The findings show cybercrime is being supercharged through “plug and play” malware kits that make it easier than ever to launch attacks.
Findings further showed that Cyber syndicates are collaborating with amateur attackers to target businesses, putting the online world at risk.
The HP Wolf Security threat team worked with Forensic Pathways, a leading group of global forensic professionals, on a three-month dark web investigation, scraping and analysing over 35 million cybercriminal marketplaces and forum posts to understand how cybercriminals operate, gain trust, and build reputation.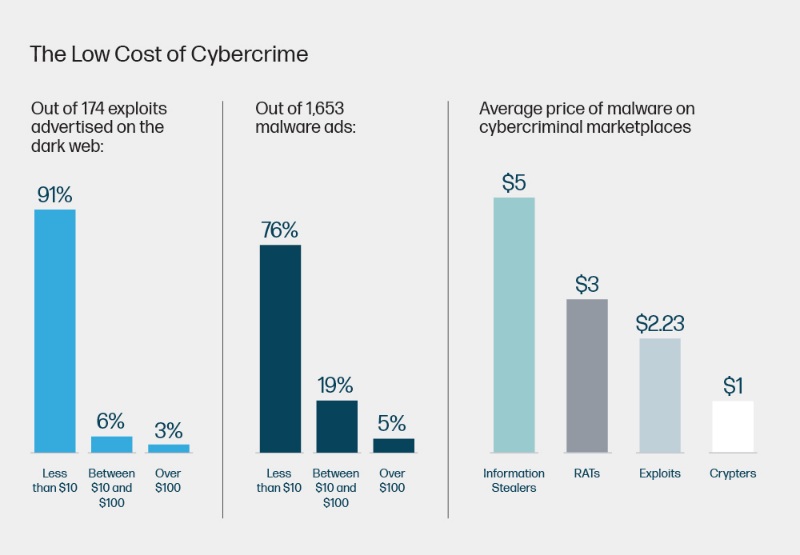
Key findings include:
- Malware is cheap and readily available – Over three quarters (76%) of malware advertisements listed, and 91% of exploits (i.e., code that gives attackers control over systems by taking advantage of software bugs), retail for under ₦4,923.17. The average cost of compromised Remote Desktop Protocol credentials is just ₦2,092.35. Vendors are selling products in bundles, with plug-and-play malware kits, malware-as-a-service, tutorials, and mentoring services reducing the need for technical skills and experience to conduct complex, targeted attacks – in fact, just 2-3% of threat actors today are advanced coders.
- The irony of ‘honor amongst cyber-thieves’ – Much like the legitimate online retail world, trust and reputation are ironically essential parts of cybercriminal commerce: 77% of cybercriminal marketplaces analysed require a vendor bond – a license to sell – which can cost up to ₦1,230,793. Eighty-five per cent of these use escrow payments, and 92% have a third-party dispute resolution service. Every marketplace provides vendor feedback scores. Cybercriminals also try to stay a step ahead of law enforcement by transferring reputation between websites – as the average lifespan of a dark net Tor website is only 55 days.
- Popular software is giving cybercriminals a foot in the door– Cybercriminals are focusing on finding gaps in software that will allow them to get a foothold and take control of systems by targeting known bugs and vulnerabilities in popular software. Examples include the Windows operating system, Microsoft Office, web content management systems, and web and mail servers. Kits that exploit vulnerabilities in niche systems command the highest prices (typically ranging from ₦393,853.76 – ₦1,723,110.20). Zero Days (vulnerabilities that are not yet publicly known) are retailing at tens of thousands of dollars on dark web markets.
“Unfortunately, it’s never been easier to be a cybercriminal. Complex attacks previously required serious skills, knowledge and resource.
“Now the technology and training is available for the price of 3 litres of fuel. And whether it’s having your company and customer data exposed, deliveries delayed or even a hospital appointment cancelled, the explosion in cybercrime affects us all,” comments report author, Alex Holland, Senior Malware Analyst at HP Inc.
“At the heart of this is ransomware, which has created a new cybercriminal ecosystem rewarding smaller players with a slice of the profits.
“This is creating a cybercrime factory line, churning out attacks that can be very hard to defend against and putting the businesses we all rely on in the crosshairs,” Holland adds.
HP consulted with a panel of experts from cybersecurity and academia – including ex-black hat hacker Michael ‘Mafia Boy’ Calce and authored criminologist, Dr. Mike McGuire – to understand how cybercrime has evolved and what businesses can do to better protect themselves against the threats of today and tomorrow.
They warned that businesses should prepare for destructive data denial attacks, increasingly targeted cyber campaigns, and cybercriminals using emerging technologies like artificial intelligence to challenge organisations’ data integrity.
To protect against current and future threats, the report offers up the following advice for businesses:
Master the basics to reduce cybercriminals’ chances: Follow best practices, such as multi-factor authentication and patch management; reduce your attack surface from top attack vectors like email, web browsing and file downloads; and prioritise self-healing hardware to boost resilience.
Focus on winning the game: plan for the worst; limit risk posed by your people and partners by putting processes in place to vet supplier security and educate workforces on social engineering; and be process-oriented and rehearse responses to attacks so you can identify problems, make improvements and be better prepared.
Cybercrime is a team sport. Cybersecurity must be too: talk to your peers to share threat information and intelligence in real-time; use threat intelligence and be proactive in horizon scanning by monitoring open discussions on underground forums; and work with third-party security services to uncover weak spots and critical risks that need addressing.
“We all need to do more to fight the growing cybercrime machine,” says Dr. Ian Pratt, Global Head of Security for Personal Systems at HP Inc.
“For individuals, this means becoming cyber aware. Most attacks start with a click of a mouse, so thinking before you click is always important. But giving yourself a safety net by buying technology that can mitigate and recover from the impact of bad clicks is even better.”
“For businesses, it’s important to build resiliency and shut off as many common attack routes as possible,” Pratt continues.
“For example, cybercriminals study patches on release to reverse engineer the vulnerability being patched and can rapidly create exploits to use before organisations have patched. So, speeding up patch management is important.
“Many of the most common categories of threat such as those delivered via email and the web can be fully neutralised through techniques such as threat containment and isolation, greatly reducing an organisation’s attack surface regardless of whether the vulnerabilities are patched or not.”
The full report can be found here: https://threatresearch.ext.hp.com/evolution-of-cybercrime-report/

