A newly uncovered database containing nearly 150 million stolen login credentials has raised alarm among cybersecurity experts.
Unlike traditional breaches where hackers infiltrate corporate systems, this leak stems from info-stealing malware that harvests data directly from infected personal devices.
The Discovery
Cybersecurity researcher Jeremiah Fowler, working with ExpressVPN, found the unsecured database online. The cache contained 149,404,754 unique logins and passwords spread across 96GB of raw data.
Each record included links identifying the platforms or services the credentials belonged to, making them highly exploitable for cybercriminals.
Scale of Exposure
The exposed accounts span some of the world’s most popular platforms:
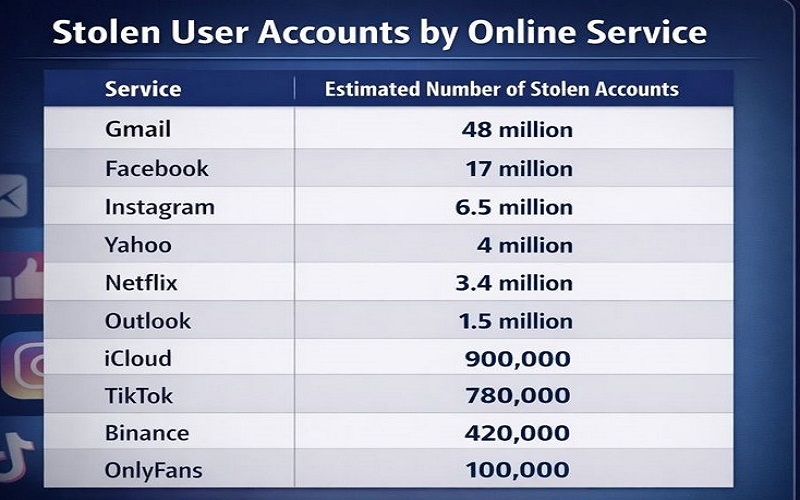
Additional credentials were linked to services such as Disney Plus, HBO Max, Roblox, and X (formerly Twitter).
Google Responds
In a statement to Tom’s Guide, Google confirmed awareness of the dataset: “This data represents a compilation of ‘infostealer’ logs — credentials harvested from personal devices by third-party malware — that have been aggregated over time.
“We continuously monitor for this type of external activity and have automated protections in place that lock accounts and force password resets when we identify exposed credentials.”
How Info-Stealing Malware Works
Unlike persistent malware designed to remain hidden on devices, info-stealers focus solely on extracting sensitive information. They capture keystrokes, passwords, and personal data, then transmit it back to attackers.
These stolen credentials are often stored in cloud databases, which, if left unsecured, can be exploited by other cybercriminals for phishing campaigns or automated credential-stuffing attacks.
Database Taken Offline
Fowler attempted to identify the database’s owner but found no information. He reported the exposure to the hosting provider, and after nearly a month of repeated attempts, the database was finally taken offline when its hosting was suspended.
Notably, the number of stolen records continued to grow during the period Fowler monitored the database, suggesting ongoing malware activity.
Why This Matters
The incident underscores the dangers of password reuse. If a victim uses the same password across multiple accounts, attackers can easily compromise several services using automated tools.
Experts recommend:
- Changing reused passwords immediately
- Using password managers to generate and store strong, unique credentials
- Adopting passkeys where available for added security
- Running antivirus software to block info-stealing malware
- Considering identity theft protection services to recover from fraud
- Finally, closing unused online accounts reduces the risk of exposure in future leaks.
The Bigger Picture
While this wasn’t a breach of Google, Meta, or other major platforms, the sheer scale of exposed credentials highlights the growing threat of malware-driven data theft.
As Fowler’s discovery shows, stolen data doesn’t just vanish — it circulates, accumulates, and resurfaces, often in unsecured repositories.
This incident serves as a wake-up call: unique, strong passwords and proactive security hygiene are no longer optional — they’re essential.

